Email security now, and email security under Google Apps
May 3rd, 2012 by dshettleEmail security has been around for over a decade, and while one might think that processes to secure email would have simplified over time, they really haven’t — if anything they’ve become more complex than ever.
The College uses a gateway system to filter incoming email — this system takes several hundred thousand messages a day, and reduces it to several thousands per day. The vast majority of incoming email is garbage: spam, malware, phishing attacks, and other annoyances. Every message goes through a complex process to determine whether or not it should actually be received by the recipient:
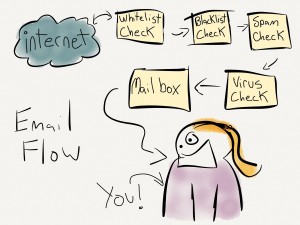 First, the message is checked against the College “whitelist”. This list is something we maintain to make sure that specific email from important, “safe” sources does not go through any other checks. If the sender is on the whitelist, they go right along to the user. If not, it’s on to the “blacklist” check. The blacklist check is a check of the sender’s computer against various free and paid databases of known-bad sources. These lists are not College maintained, we get them as a service. Sender computers on blacklists get blocked right away, but if they are not on the blacklist, they move on to the spam check, or the word & phrase filters.
First, the message is checked against the College “whitelist”. This list is something we maintain to make sure that specific email from important, “safe” sources does not go through any other checks. If the sender is on the whitelist, they go right along to the user. If not, it’s on to the “blacklist” check. The blacklist check is a check of the sender’s computer against various free and paid databases of known-bad sources. These lists are not College maintained, we get them as a service. Sender computers on blacklists get blocked right away, but if they are not on the blacklist, they move on to the spam check, or the word & phrase filters.
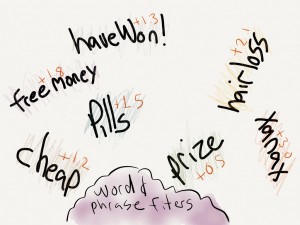 The spam filter scans the message for specific attributes that are common in spam, such as specific combinations of words and/or phrases. Each “hit” on a given word, phrase, or email attribute adds points to the spam rating of the message. Once completed, the total score is evaluated. Any message with a score greater than or equal to 6.5 goes into the trash.
The spam filter scans the message for specific attributes that are common in spam, such as specific combinations of words and/or phrases. Each “hit” on a given word, phrase, or email attribute adds points to the spam rating of the message. Once completed, the total score is evaluated. Any message with a score greater than or equal to 6.5 goes into the trash.
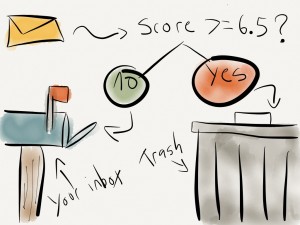 Most real email messages score somewhere between 1 and 4. The 6.5 threshold has to be periodically adjusted, and the whitelist constantly tweaked. Scores for word and phrase combinations also need to be manipulated. If we’re too conservative, we get lots of spam in our inboxes. If we’re too aggressive, we start blocking legitimate email. After scoring, it’s on to a quick virus check, then if all is well, your mailbox.
Most real email messages score somewhere between 1 and 4. The 6.5 threshold has to be periodically adjusted, and the whitelist constantly tweaked. Scores for word and phrase combinations also need to be manipulated. If we’re too conservative, we get lots of spam in our inboxes. If we’re too aggressive, we start blocking legitimate email. After scoring, it’s on to a quick virus check, then if all is well, your mailbox.
Over the years we’ve found the right balance, and we constantly strive to maintain it. But this balance is time consuming, imperfect, and ultimately less effective than new cloud-based solutions like Gmail. How does the above look when we “go Google”? More like this:
 They do all the work, and from most people’s experiences, they do it better than we do. In addition, we’ll be purchasing Postini services from Google to further enhance the security of our email, so by most accounts, email will be easier to manage, more available, and more secure.
They do all the work, and from most people’s experiences, they do it better than we do. In addition, we’ll be purchasing Postini services from Google to further enhance the security of our email, so by most accounts, email will be easier to manage, more available, and more secure.